Let’s talk about something really important that you need to be aware of: the Magento APSB24-40 security patch.
Now, I know what some of you might be thinking. "Another security patch? Don't we have enough of those already?" And you're right, as it can feel like we're constantly chasing our tail at times with these updates. But this one is one of the more critical updates to be aware of.
Released in June 2024, this patch addresses several vulnerabilities in both Adobe Commerce and Magento Open Source. But this patch introduces some major changes to how Magento handles Content Security Policy (CSP), and these changes directly impact functionality around the checkout.
I've been working with Magento for a while, and I've seen first-hand how updates like this can catch people off guard. But whether you're running a small boutique store or managing a large eCom operation, understanding and implementing this patch is absolutely crucial for keeping your site secure and running smoothly.
The Evolution of APSB24-40
The journey of the APSB24-40 patch really demonstrates the importance of staying on top of security updates. When Adobe first released this patch on June 11, 2024, it was classified as a Priority 3 update - important but not urgent. However, within just a few weeks, the priority level escalated rapidly.
By June 26, Adobe had bumped the patch up to Priority 2, indicating that it should be installed within 30 days. Then, on July 8, they made a critical announcement: APSB24-40 was now a Priority 1 update, the highest level possible. This meant that the vulnerabilities were being actively exploited, and the patch should be installed as soon as possible (ideally within 72 hours).
This rapid progression underscores how quickly security can change in eCommerce, and how crucial it is that store owners and developers are always ready to act relatively fast when these critical updates are posted.
With that context in mind, let's dive into what this patch actually does and why it's so important, starting with how it changes Magento's approach to Content Security Policy.
Understanding Content Security Policy (CSP)
Let's talk a bit about Content Security Policy, or CSP for short. If you're not familiar with it, don't worry; let’s break it down a bit.
You can think of CSP as a security guard for your website. Its job is to control what types of content are allowed to load and execute on your web pages. It does this by defining a set of rules that the browser must follow.
Why does this matter for Magento? Well, CSP is one of the most effective ways to prevent cross-site scripting (XSS) attacks. These attacks happen when a malicious actor finds a way to inject their own code into your website. This code could do nasty things, like steal customer data or disrupt your checkout process, and it’s a super large security concern.
CSP works by specifying which types and sources of content can be trusted. This includes things like scripts, styles, images, and so on. If a piece of content doesn't come from a trusted source, CSP blocks it. It's like the security guard saying, "Sorry, your name's not on the list. You can't come in."
However, implementing CSP is not so straightforward. If your policies are too strict, you might accidentally block legitimate content, causing parts of your site to break. On the other hand, if your policies are too loose, they might not provide adequate protection.
Cautionary note: Google recently released a whitepaper about CSP whitelist ineffectiveness. While this is a concern, maintaining proper
csp_whitelist.xmlfiles for your Magento site is still important; it’s effectiveness isn’t immediately and completely obliterated by the release of a whitepaper. While security around CSP can be improved, security works best when implemented in layers. Every additional layer of security increases its effectiveness, and continuing to have a CSP in place is no exception.
Key Changes in APSB24-40
The most significant change is how CSP is applied to the Magento checkout process. Before this patch, CSP was running in "report-only" mode when both creating an order through the admin panel and the checkout on the storefront. This means that if a piece of content violated the CSP policy, Magento would log the violation but still allow the content to load. This was useful for identifying potential issues without risking breaking the checkout process.
However, the APSB24-40 patch changes this. With this update, CSP in the checkout now runs in "strict" mode by default. This means that instead of just logging violations, CSP will now block any content that doesn't comply with the policy. This is a significant shift towards better security, but it also means that if you have any customizations or third-party extensions that aren't CSP-compliant, they might stop working in the checkout.
Another key change is how inline JavaScript is handled. Inline scripts are pieces of JavaScript code that are directly embedded in the HTML, rather than being loaded from a separate file. In the past, Magento allowed these scripts to run without many restrictions. However, inline scripts are a common vector for XSS attacks. The APSB24-40 patch now disables inline scripts by default in the admin when creating an order, or checkout out on the frontend.
This change improves security, but it might also impact any custom functionality you've built that relies on inline scripts. If you have customizations like this, you'll need to find alternative ways to implement that functionality that are CSP-compliant.
The patch also introduces a new dependency between the checkout module and the CSP module. This means that if you had previously disabled the CSP module for any reason, you might encounter issues after applying this patch.
These changes represent a significant step towards a more secure default configuration for Magento. However, they also require us, as developers and store owners, to be proactive in ensuring our customizations and extensions are compatible with these new stricter policies.
Impact on Checkout Functionality
The shift to strict CSP mode in the checkout is a double-edged sword. On one hand, it significantly enhances the security of this crucial part of your store. On the other hand, it can cause unexpected issues with customizations and third-party extensions.
For example, let's say you have a custom extension that adds a loyalty point redemption feature to your checkout, and it uses inline JavaScript. After applying the APSB24-40 patch, this feature would likely stop working, because inline scripts are now blocked by default.
Similarly, if you use a third-party extension that integrates with a shipping provider to display real-time rates in the checkout, and this extension relies on injecting scripts from the provider's domain, it may break if those scripts don't comply with your new CSP policy.
Even if you don't have any custom code, you might still encounter issues due to third-party extensions. Many popular payment gateways, analytics tools, and other services provide Magento extensions to integrate with your store. If these extensions aren't updated to comply with the new CSP rules, they may cause problems in your checkout.
These potential issues aren't just theoretical. When this patch was released, many Magento store owners reported problems with their checkout immediately after applying the update. The severity ranged from minor visual glitches to complete checkout failures, preventing customers from placing orders.
Challenges for Magento Stores
Implementing the APSB24-40 patch can present several challenges for Magento store owners and developers. These challenges primarily stem from the significant changes to how CSP is enforced and the potential for unexpected issues after applying the update.
One of the biggest challenges is for stores that had previously disabled the CSP module. It was not uncommon for developers to turn off CSP to avoid dealing with additional security conflicts and warnings. However, with this patch, the checkout module now depends on the CSP module being active. If you apply the update without re-enabling CSP, you might find that your checkout stops working entirely.
While there are solutions out there such as Yireo_DisableCsp and Disable CSP Shim, I do not recommend installing these types of modules. While CSP is just one layer of security, and at times may not be completely effective, there is overwhelming proof that every additional layer of security you can add to your store will improve the overall security of your store. It’s much better to learn how CSP works and how to implement it, rather than simply disabling it because it’s a hassle to deal with.
Another challenge with CSP is identifying and updating any custom code that relies on inline JavaScript in the checkout. With strict CSP enforcement, these scripts will be blocked, potentially breaking important functionality. This requires a thorough audit of your checkout process and any customizations you've implemented. You'll need to find alternative ways to achieve the same functionality that comply with CSP.
Third-party integrations can also present a challenge. Many payment gateways, analytics tools, and other services rely on injecting scripts into your checkout. If these scripts don't comply with your CSP policy, they'll be blocked, which could break the integration. You'll need to work with your third-party providers to ensure their scripts are CSP-compliant.
The rapid escalation of the patch's priority level also presents a challenge. With the patch going from a low priority to a critical priority in just a few weeks, many stores may have felt pressured to apply the update quickly. This can lead to rushed implementations without thorough testing, which increases the risk of unexpected issues affecting your live store.
To overcome these challenges, you need to have a systematic approach ready to go. This includes carefully testing patches within staging environments, auditing your custom code and third-party integrations, and having a rollback plan in place in the event there are issues on production. You'll also need to ensure all stakeholders and third-party providers are aware of upcoming changes in the Magento ecosystem, and are prepared to update their integrations if necessary.
While these challenges can seem daunting, they're not insurmountable. With careful planning and execution, you can successfully implement the APSB24-40 patch and enjoy the security benefits it provides.
Implementing the Patch Safely
Alright, so we've talked about the changes in the APSB24-40 patch and the potential challenges they present. Now, let's discuss how you can implement this patch safely to minimize disruptions to your store.
The first and most important step is to create a full backup of your Magento store and database. This is your safety net. If anything goes wrong during the update process, you can always restore it from this backup.
Next, apply the patch to a staging or development copy of your store first (you do have a staging environment set up for your Magento store… right?). This allows you to test the update in a safe environment without risking the updates affecting your live store. Since staging should be an exact replication of production in terms of installed server software and the like, there should be no surprises. Having a solid staging environment available is a best practice not just for this update, but really any update that is to be deployed to your store.
Before applying the patch, review your current CSP settings. Check if you have the CSP module enabled, and be sure to take notes about any custom policies you've set up. This will give you a baseline to compare your site against after the update is complete.
When you're ready, apply the APSB24-40 patch following Adobe's official instructions. If you had previously disabled the CSP module, be sure to re-enable it before testing out the patch.
After applying the patch, thoroughly test your store, and pay special attention to the checkout process. Test all payment methods, shipping options, discount codes, and any custom features. Essentially, you want to simulate as many real-world scenarios as possible to catch any potential issues. Deploying patches to your store should never introduce breaking changes on production.
If you encounter any issues, don't panic. Check your browser's console and the server logs for any CSP violation reports. These reports will help you identify which scripts are being blocked and where they are coming from. You can then work on updating those scripts to comply with your new CSP policy. If there are issues on production that weren’t happening on staging, it’s a sign that your staging environment is failing its purpose, as staging should always be a 1:1 simulation of your production environment.
If you find that the update did cause critical issues with your checkout and you need to restore functionality quickly, or if you needed to upgrade Magento to the latest version but really wanted to bypass these CSP updates, there is a temporary workaround.
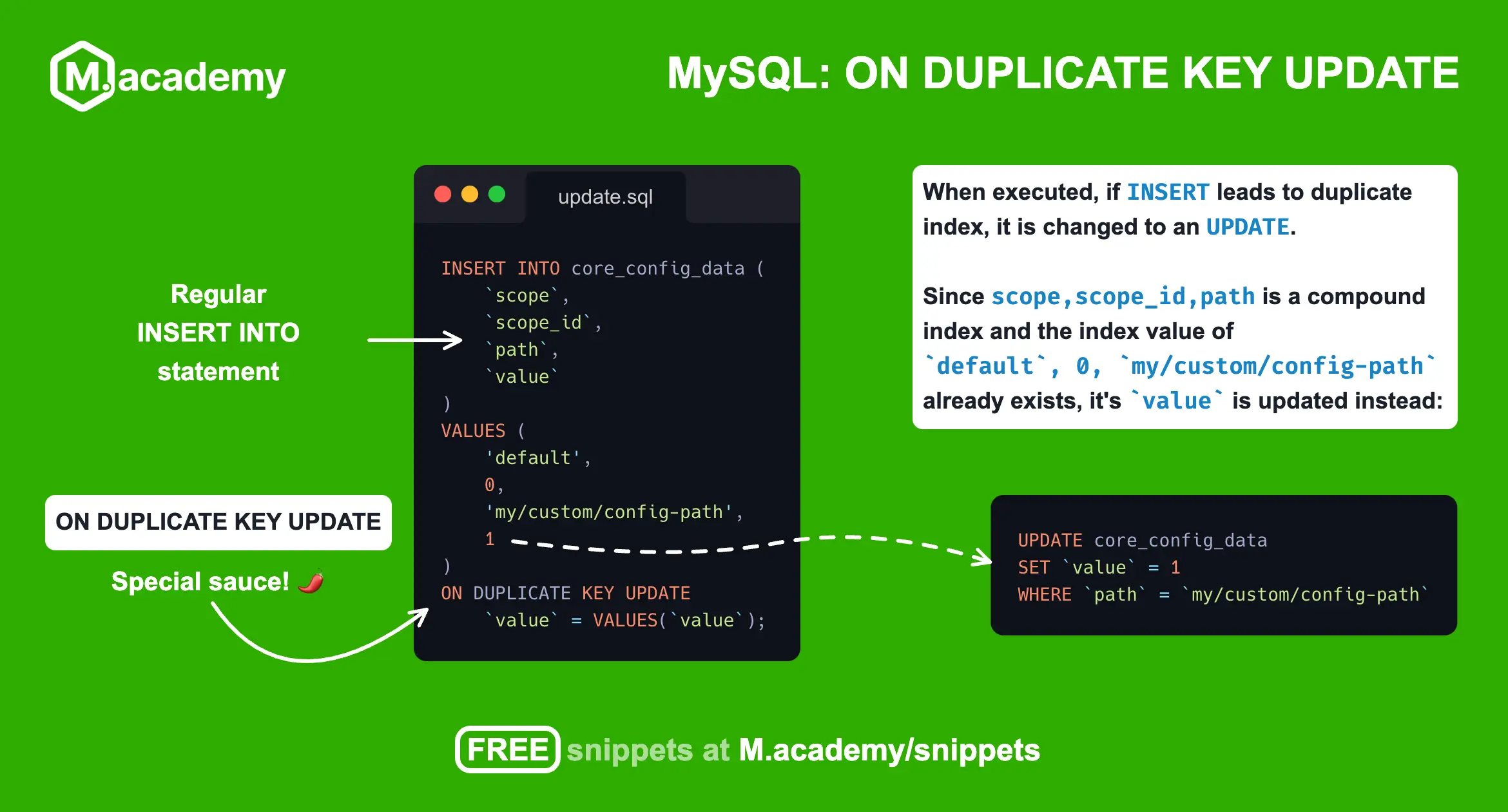
You can revert the checkout CSP back to "report-only" mode by running this specific SQL command:
INSERT INTO core_config_data (
`scope`,
`scope_id`,
`path`,
`value`
)
VALUES (
'default',
0,
'csp/mode/storefront_checkout_index_index/report_only',
1
)
ON DUPLICATE KEY UPDATE
`value` = VALUES(`value`);However, please note that this should only be a temporary solution. The goal should be to update your store to work with the stricter CSP rules. Magento had several open security holes before this patch was introduced, and this update closes them up.
Also of note is that normally you would use Magento’s built-in bin/magento config:set command to save a new config value, but since the csp/mode/storefront_checkout_index_index/report_only config path doesn’t match Magento’s standard format, and will throw an error saying:
The "csp/mode/storefront_checkout_index_index/report_only" path doesn't exist. Verify and try again.
This means that you’ll need to run the above direct SQL query in order to update this configuration value. Relatedly, in order to update all environments with this same setting and avoid the potential of human error when running SQL scripts by hand, you should consider creating a data patch within a custom module which applies this SQL query through code, rather than running it directly on the MySQL server.
Best Practices for CSP in Magento
Now that we've covered how to implement the APSB24-40 patch, let's take a step back and look at some general best practices for managing Content Security Policy in your Magento store.
First and foremost, keep CSP enabled. I know it can be tempting to disable CSP to avoid dealing with potential issues, but that's like leaving your store's front door unlocked to avoid having to find your keys. CSP is a critical security feature, and it's important to keep it active.
While you can probably disable CSP and still currently be PCI compliant (it’s a great area… be careful!), this could raise questions in a PCI audit and probably isn’t a good idea. You'd need to demonstrate that you have implemented other effective measures to prevent the types of attacks that CSP is designed to mitigate (particularly XSS attacks), and will most likely need to document your alternative implementation and the reasoning behind making such a change. Also, new PCI 4.0 requirements require verification of script integrity on payment pages, so you should be very aware of these updated guidelines as well.
Managing CSP is an ongoing process. As you add new features, extensions, or integrations to your store, you'll need to update your CSP policies to accommodate them. Make it a habit to review your CSP settings regularly as part of your regular maintenance routines (you do have regular maintenance processes in place… right?). To make this process easier, you can use tools like the Magento CSP Whitelist Generator to quickly generate the necessary XML configurations.
When you do need to add a new source to your CSP whitelist, be as specific as possible. Avoid using wildcards or overly broad domains. The more specific your list, the more effective your CSP will be at preventing unauthorized content.
If you're unsure about a particular policy change, use the CSP "report-only" mode. This allows you to test a policy without actually blocking any content. You can review the violation reports to identify any unexpected issues before enforcing the policy.
On that note, make sure you're regularly monitoring CSP violation reports. These reports can alert you to potential misconfigurations in your policies, but they can also help identify attempted attacks. If you see a sudden spike in violations from a particular source, it could be a sign of a malicious actor trying to inject unauthorized content into your site.
If you're working with a team of developers, ensure that everyone understands CSP and its implications. It's easy for a developer to inadvertently introduce a script that violates your CSP policy if they aren’t familiar with how it works. Providing CSP training and guidelines can help prevent these issues.
For a general overview of how CSP works in Magento, check out the related Magento CSP Architecture documentation.
CSP is just one piece of your security layer. Other critical security practices include keeping your Magento software and all extensions up to date, performing regular backups of your site and database, and enforcing strong authentication for admin users. By implementing these measures alongside a robust CSP strategy, you can significantly enhance your store's overall security posture.
By following these best practices, you can maintain a strong security posture for your Magento store while still providing a smooth, uninterrupted experience for your customers.
Key Takeaways
- The APSB24-40 patch significantly changes how Magento handles Content Security Policy, especially in the checkout process, enforcing strict mode by default and disabling inline scripts.
- The rapid escalation of the patch's priority level underscores the importance of staying informed about and acting quickly on critical security updates, and having a stable process in place to apply similar updates in the future.
- The patch enhances security but may impact custom functionality. Thorough testing and preparation are crucial to mitigate potential issues.
- A temporary workaround exists to revert checkout CSP to "report-only" mode, but this should only be a short-term solution, allowing you to resolve any issues before enabling the core CSP rules long-term.
- Managing CSP is an ongoing process that requires regular reviews and updates as your store evolves.
- The APSB24-40 patch is just one part of a comprehensive security strategy that should include regular updates, strong access controls, and adherence to best practices.
Managing an e-commerce store can be challenging, especially when it comes to balancing security and functionality. But by staying informed, being proactive, and following best practices, you can navigate these challenges successfully.
Next steps
Ready to really start mastering Magento? Check out these valuable tips and resources:
- Add a host to the content security policy XML (Free video lesson)
- Grow your Magento expertise with all courses & lessons (500+ students)
- Browse the courses and level up your Magento skills